Cyber threat analysis is the process of assessing the cyber activities and capabilities of unknown intelligence entities or criminals. A cybersecurity threat or “cyber threat” can be defined as a malicious act that seeks to disrupt digital life. This act could be the disruption of a communication pathway, the damage of data, or stealing data.
Hackers target enterprises, governments, institutions, or even individuals with valuable information. Threats posed by cyber-attacks include denial of service attacks (DoS), computer viruses, malware, phishing emails, and others. The attacks target anyone with an online presence. Cyber-attacks can lead to electrical blackouts, breaches of government security details, failure of military equipment, disruption of computer networks, paralyzation of phone networks, unavailability of confidential data and it may affect the functioning of human life.
Cyber-threats increase day-after-day as the technological advancement in artificial intelligence or intelligent systems facilitate the need for better skills to by-pass highly secure systems. For these reasons, organization leaders must complete a thorough and detailed cyber threat analysis to know the extent of exposure of their business or enterprises to cyber-attacks.
The main objective of cyber threat analysis is to produce findings used to aid in initialization or support of counter-intelligence investigations. Then action is taken to eliminate the threat from the given organizations, business, or government system. In cyber threat analysis, the know-how on external and internal information vulnerabilities relating to a particular business model is matched against the actual or real-world cyber-attacks. This type of approach to countering cyber-attack is a desirable transition from a reactive security state to an efficient, proactive state.
The final output from a threat assessment should provide the best practices on how to utilize the protective controls to promote integrity, availability, and confidentiality, without affecting the functionality and usability conditions.
Components of the Cyber Threat Analysis Process
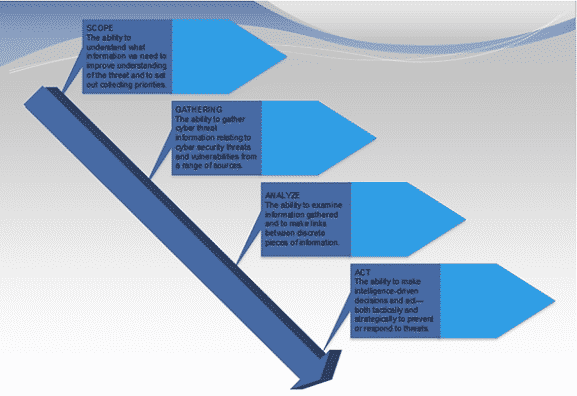
1. Scope
The scope of the cyber threat analysis states what will be included and excluded from the analysis. Included items are those items that should be protected from the threat.
The first step in any cyber threat analysis should be to identify every susceptible item that must be protected from access by malicious third parties. After this, the level of sensitivity and the desired degree of protection of the item is drafted and extensively defined by the analysis drafters.
2. Collection of Data
In every well-structured organization, there are procedures and policies to guide how people, machines and other components of an organization are expected to operate. All these need to be clearly stated out for compliance purposes.
In reality, close to 25% of organizations fail to meet the minimum security standards put in place. The Senior VP of Hewlett Packard, Art Gilland, stated that most organizations fail to meet the required security standards because they are in a rush to meet a policy. Organizations tend to “check boxes” for compliance instead of implementing protective measures to the levels defined by the scope of the threat and the exposed item.
In the Collection of Data stage, the first step is to collect information about the actual cyber-attack or threat incidents. Examples could be phishing email header and content, uncovered hostile command and control infrastructure of IP addresses and domain names, URLs to malicious links, and so on. One must distinguish between real potential attacks and threats that are not real but are perceived threats. The scope should help filter out percieved threats in order to ensure that the focus is on the targeted threats that exist in reality.
In order, to transform data into intelligence, an information technology analyst must be granted unrestricted system access. Research can be sourced from many places including internet searches, intrusion incidents, firewall logs, digital forensic analysis, reverse engineering of malware, digital forensic analysis, detection system logs, honeypots etc.
Corporate procedures and policies should be analyzed and a thorough investigation should be done to determine whether they meet the compliance standards or level in the organization.
3. Vulnerability Analysis of Acceptable Risks
In this phase, the analysts test what has already been gathered in order to determine the extent of current exposure. The existing security defense is tested to determine whether it has the capability to neutralize information threats in terms of integrity, availability and confidentiality. This stage should double check whether the current policies, security measures and policies are adequate protective measures. Penetration tests are also done as part of vulnerability analysis in an attempt to identify vunerabillites.
Fig. 2
When a cyber-attack encircles the rings of protection
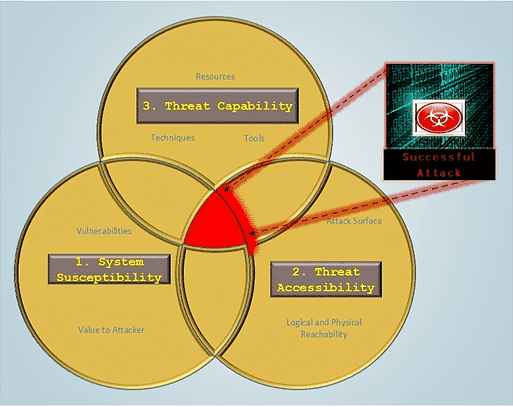
Threat analysis is a continuous process and not an occasional or a one-time event. It is an ongoing process that ensure that all safeguards work properly. Risk evaluation should be incorporated as an integral part of an organization so that it becomes part of the overall life cycle. This helps in identifying risks that might have not yet reached their full blown stage, where they cause maximum damage and loss to the organization.
4. Mitigation and Anticipation
After completion of all other previous steps, a highly qualified analyst can then use the corpus of threat data identified to determine preventive measures. The analyst has the task to catigorize the threat data into groups, allocate each pattern to specific threat actors, and implement mitigation measures. Subsiquently, the analyst must anticipate the occurrence of similar attack in the future.
Methodology
Threat models and metrics included in this section are meant to aid in characterization of specific threats hence fulfilling the elementary purpose of threat analysis.
1. Threat Metrics
Understanding how anomalies and trends occur can be used to facilitate the threat analysis process when an accurate measurement of events is done. It can also underline the ability of certain type of threats. This is done by joining the missing dots between the experienced threats and the possible consequences. In short, qualitative threat measurement techniques and process should give precise results concerning risk management. Defining and applying threat measures of acceptable quality is a practice that does not have maturity and consistency in its nature of execution.
Metric can be defined as a unit of measure. On the other hand, measure is a definition for a given hallmark of performance. For instance, if a threat is perfectly measured in a consistent way, with the help of a good metric that is clear and unambiguous as well, then the analysist is most likely to upgrade his ability to understand that threat, affect, control and defend against it for a given period of time. Decision making as per the correct interpolation is much simpler if the nebulosity is not extremely dark.
An ideal example of an appropriate quantitative portrayal in cyberspace is the number of intrusions or attacks per month. When these figures are taken for a long stretch of time, they can reveal the capability and intent of the adversary. This gives an analyst the task to properly calculate all the possible risks and further allocate resources required to sort it out.
2. Threat Models
A threat model is basically a well-organized representation of all the necessary information that affects the security of a system, application or network server. This can be simply termed as the view of an information technology via a security glass. capturing, organizing and analyzing all the gathered information in an understandable and logical order is known as threat modelling. To do this sufficiently, a combination of metrics known as measurement framework is preferred instead of a stand-alone metric. This is because of the incapability of the latter to encapsulate behavioral characteristics of the complex actors or systems.
In addition to the definition given at the beginning, a threat can be considered as a malevolent actor with specific personal, political or social goal intended to oppose an accepted social norm, a private enterprise or an established government. The actor in this case is can be an organization, institution or an individual with self-centered interests to satisfy. A model on the hand, is a simplified representation of something. Therefore, a threat model is a combination of the two definitions, in that, it gives prominence to details relevant to the threat.
Using consistent threat model in threat analysis promotes consistency as well as reduce the detrimental effects of personal bias and preconceived opinions and notion. As time goes by, data acquired continues to pile up while index of success rate also intensifies. Due to such reasons, inter alia is strongly advised to keep clear a trackable record of data stored in a continuous manner. Properly documented data acts as reference database that can in turn be used by other cyber-security experts.
Threat Modeling Process
Sample No. 1
Risk assessment and threat modelling process takes place in three major steps:
- Assess risk – determine the amount you are to lose from the assessment
- Determine potential threats – state out various things that your system does that can possibly be attacked including what libraries and frameworks do for you.
- Mitigate threats – make sure that the parts of your code that are susceptible to attack are well protected.
Threat Modelling Process
Sample No. 2
Below is an overview of the threat modeling process
- Identify assets – point out each and every asset that must be protected.
- Come up with an architecture overview – use tables and relatively simple diagrams to document the architecture of your system. Other components to be included include trust boundaries, data flow and subsystems.
- Breakdown the application – breakdown the architecture of your application including the underlying host infrastructure design so as to come up with a security profile for the system. The primary objective creating a security profile is to uncover each and every vulnerability in the system’s design, configuration or implementation.
- Identify the risk – having the attackers goal in mind as well as know-how on the architecture and potential vulnerabilities of your system, distinctively identify the risks that could definitely affect the system or application.
- Logically document the threats in an organized manner – use a common threat template to capture the attributes specific to each and every threat.
- Rate the threat – arrange the threats in order of the potential damage that they are capable of causing to the system such that the most significant threats come first.
The Generic Threat Matrix
In this method, an analyst uses necessary threat attributes to characterize the type of risk based on the overall nature of the threat. By using this kind of characterization, an analyst is able to fully describe the threats without conforming to the preconceived notion. To get this better, we can define matrix as a framework or a model used to organize a set of other related metrics into the desired structure. The matrix is graduated into levels of magnitude where, each level corresponds to a unique threat.
1. Threat Attributes
Threat attribute is an independent feature of a threat and are of two dominant groups;
Commitment Attribute Group
A commitment is a pledge that confines an individual to some course of action. Applying the same, attributes in commitment group are attested to the unconditional willingness of the threat to attain its specific goal. For a higher level of commitment, the threats virtually stop at no obstacle to achieve their aim. Attributes are classified into 3 groups:
- Stealth (Question: Does the organization have any verified information concerning the threat?)
- Time (Question: how much time is the threat willing to invest?)
- Intensity (Question: To what extent is the threat willing to go?)
Resource Attribute Group
The attributes in this category shows the amount of resources that a threat can deploy. Unlike in commitment attribute group, here, a higher value of magnitude denotes that the threat is more sophisticated hence it can easily attain its goal easily.
Resource family is also made up of three attributes:
- Access (Question: How efficient is the ability of the threat actor to compromise the system?)
- Technical Personnel (Question: How many individuals is the threat using to further its ends?)
- Knowledge (Question: What level of skill drives the threat engine?)
Threat Matrix
2. Attack Vectors
This is the path or route used by a threat to gain access to a system, network or a device, primarily, to launch a cyber-attack, plant a malware, gather relevant information, etc. Attack vectors are as follows:
- Mobile devices
- Unsecured wireless networks
- Phishing attacks
- Removable media
- Malicious web content
- Malware and viruses
3. Target Characteristics
The rate at which targets are hit by threats vary because some are more vulnerable and attractive than others. The frequency of attack on a target is also a significant information to be expressed in metrics.
4. Attack Trees
Attack trees concept is a structured and hierarchical way to logically collect and document the anticipated or likely attacks on a given system. The tree decomposes the threat agents depending on the type of attack each agent utilizes.
Fig 3
Creating attack trees
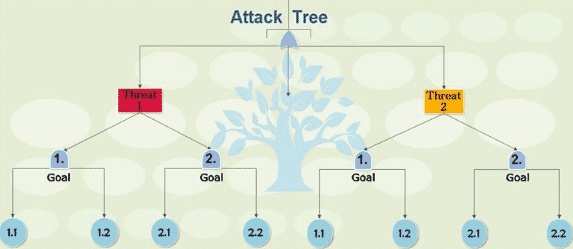
Pros of attack trees
- It provides a direct and transparent mode for analysis of attack agents
- The model encourages the use of deductions or conclusions which can be harnessed for quality output.
- They are highly flexible, hence can cover the entire spectrum of threats and attack agents in the entire platform.
- It is compatible with other models and data from attack trees can be used in analysis using a different model.
- Attack Frequency
This is an indicatory metric that can be used in conjunction to data corresponding to the degree of an attack. The idea of pairing vulnerability index and frequency metric can also be considered while using attack tree model for threat analysis.
The Threat Analyst Position and Assessment Abilities
A threat analyst is responsible for the determination of the level of risk within their organization based on both risk and vulnerability assessment. The threat analyst defines what security measures need to be enforced and which ones are ineffective and should be discarded. The measures should not be exaggerated as this may lead to overprotective controls that result in higher initial installation cost and unecessarily high maintenance costs.
Threats and the nature of attacks continue to evolve with technological advancement. Millions are spent on inovation and training. Becoming a strong technical expert is the only way to combat the rapidly mutating cyber-attacks. Continuous practice and constant learning using books, blogs, and journals is required master your security skills in information technology. Hard work is required to becoming an elite analyst who can effectively deal with encountered security issues.
The data used in analysis is usually outsourced from intelligent products which require technical skills for interpretation. The threat analyst must possess skills to read and interpret data from security events. The analyst should have technical writing skills to prepare a report of their findings. These capabilities are often less of a science and more of an art.
Conclusion
Cyber threat analysis is a continuous process that should be carried out frequently to ensure that security measures work effectively as per the intention. This is because of the rapidly changing technology and other factors that affect cyberspace such as political factors, social factors and so on and so forth. Organization that do not perform threat and risk analysis are left open to attack by cyber pests which can lead damage of their business forever. In cybersecurity hemisphere, nothing is more detrimental than the feeling of being vulnerable as it leaves you with no option but to trust that your lucky star will magically extend its reach to patch up every loop-hole in the system that threats infiltrate through.